
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Gaeilge
Gaeilge  اردو
اردو  Indonesia
Indonesia  Polski
Polski Identory antidetect tool tailored for people dealing in the areas of traffic arbitration, SMM, SEO, E-commerce, and programming. The most important feature that one selects the Identory for is the ability to create a unique digital fingerprint for every separate profile. This means that users can bypass geo blocks on target resources, partake in multi-accounting, and escape profiling by anti-fraud systems which employ bots. Let’s try to understand more about what is Identory and analyze which functionality of this software is crucial for accomplishing tasks in the mentioned areas.

The Identory browser has the ability to manage a large number of profiles for both individual and team work. Every profile can be configured as a separate unique workspace and team members can use them simultaneously. Here are few other main capabilities:
A bulk management functionality is included for starting and stopping profiles, as well as setting and deleting them, all of which ensure that bulk changes can be made quickly. We will further explore the key functionality, as well as provide a brief Identory interface overview.
When someone uses the Internet, they are identified through an online user ID, which is a unique set of digital fingerprinting parameters. The Identory allows modification of parameters to make the connection more anonymous. The user's fingerprint which also includes the data and can be edited is composed of:
Among the Identory browser features is the existence of a comprehensive repository of pre-built hardware configurations, which ensures that as such, the chances of authenticity being questioned is next to none. The user can select from over a million potential combinations of hardware specifications. Moreover, there are also fingerprints of mobile devices that can be employed for the purpose of mobile operating system virtualization.
The intricate fingerprint switcher helps to cover up the operating system's identity and prevents data leaks through the web API of the browser and the network connections for added security.
Since all profiles are unconnected, after being set up in the antidetect, the security systems of trading platforms, social media, and streaming services would not be able to link or cross-reference them or take counteractive steps like issuing IP blocks. Users can perform tasks like automation, multi-accounting, and mass actions completely anonymously.
When talking about Identory, special attention should be given to its features that are focused on user privacy protection. Such functionality includes:
These measures combined ensure a high level of security and confidentiality on the internet by minimizing the chances of users being tracked for their activities.
These features enable the easy, efficient management of multiple profiles by providing access through a friendly interface. Access to essential functionalities does not get buried under excessive elements and allows the user to easily use the workplaces.
The user's account and subscription information is displayed in the upper tab, along with a menu for notifications, settings, language, and theme selection.

Now, let's examine the main tabs in the further interface Identory browser review.
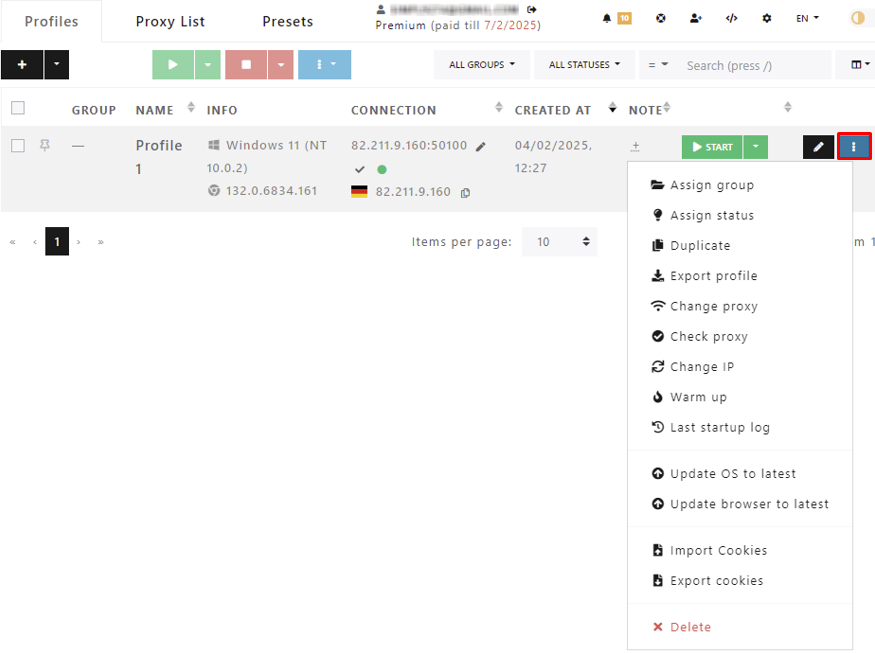
Users can manage profiles by creating new ones, editing, or deleting them in this section. The user can also filter profiles by status, set tasks to profiles, stop or launch tasks, and search for profiles manually. The interface also provides bulk, one-time, and import
functionalities, as well as delete and edit options. To ease identification of profiles, the user's group name, connection details, profile name, creation date, and other information are displayed in the main menu.
The main menu columns can also toggle, meaning the workspace can be personalized so that only relevant information is available to the user.
This menu is for completing tasks related to the management of proxy servers. Each profile is assigned a unique IP address by linking it to a proxy server. Proxies may also be added one by one, or imported in bulk and sorted into groups for easier management, and monitoring the quality of the connection can be performed. Just like the “Profiles” tab, this one can be modified as well.
When adding the proxies, there are different modes of settings to select from, be it via quick line insertion or manual addition. If there is a link that updates dynamically for mobile or residential proxies, it can be added in this menu and used directly from the main window using the “Change IP” button.
Primarily designed to facilitate rapid profile creation, presets are configurations that have already been set for all profiles. In the tab, the user sets up a profile, creates a preset, and saves it so it can be used and adjusted in the future. This saves a lot of time since ready-made settings of the device and user environment parameters can be utilized instead of needing configuration from scratch.
Besides serving the preset purpose, they are convenient as a starting point that can be modified for specific tasks.

Windows, Mac OS (including devices with Intel and Apple Silicon), and Linux systems all support using Identory browser. Due to the cross-platform nature of development, the software functions as expected and interacts with different system resources correctly regardless of the operating system in use.
Identory is capable of self-adapting to suit the operating system environment, for instance, network drivers and graphics subsystems. This guarantees stable operation on any device. The Identory interface is proprietary and serves all users' devices equally, thereby ensuring the same level of performance for all.
When managing a multitude of accounts on a single website, there are risks involved, such as account blocks. Some websites can track when a user logs into different accounts at the same time, which can lead to profiles being banned, even when all accounts have separate configurations. In those scenarios, the Identory browser provides sufficient protection against profile data leaks, thus, diminishing the chances of being blocked on various websites. This is achieved by the ability to start and stop several profiles at once.
For this purpose, Identory's tools, Shuffled profiles, which change the order in which profiles are launched, as well as start with random interval, which sets a random time frame to launch between profiles, are designed. They are the same when launching profiles and ensure safety during the halting of profile covers.
Furthermore, the "Paste as human typing" option helps protect accounts against anti-fraud systems while still giving users a good level of protection for their accounts. While it assists with quick data entry by copy-pasting, it also has the ability to allow users to appear as if they are entering data manually. This is crucial, for instance, when creating Gmail accounts since Google does monitor if the information is entered by hand or is just pasted.
These functions serve to strengthen the overall Identory browser security while working with multiple profiles simultaneously.
The application performs quite well on all parameters because of its advanced engine and effective resource management. Also, the app manages parallel processes without instability, which is useful when working with many different profiles.
The antidetect Identory browser does not experience loss of speed which is common when using such features, because of the advanced features of it’s engine such as:
The smooth and fast switching between profiles is also achieved due to segmented profile dependent processes and gradual information transfer with secondary storage devices. The browser also benefits from enhanced memory management, allowing responsive performance with high volumes of simultaneously opened profiles.
The correct functioning of the browser on popular web resources such as social media, streaming services or e-commerce websites shows that it is stable. This is done using correct emulation of real device parameters; for most sites, such a profile represents a valid user. The app engine is also able to carry out scripting for pages that use advanced techniques to try and block the user through some JavaScript activity control mechanisms.
The software support of new site standards such as the HTML5 markup language and the new security HTTPS guarantees not only the usage and access to most sites but also safe interactions with them.
To summarize, the Identory browser performance allows them to work lag free, page correctly, and circumvent any anti-fraud mechanisms unobtrusively which is very useful to them.
Before considering how to use Identory, it is necessary to familiarize yourself with the available pricing plans. It is worth noting that anti-detect does not have a trial version or free tariff, but the following options are available:
To note, “Starter” encompasses all the important features of the “Premium” plan. Unlike other plan limits, profiles under this plan have no restriction.
Below are a few simple steps on how to install the Identory app:


Core functionalities will remain locked until the user pays for a subscription. An account can be set up through the official page or directly through the interface.
Let us explain how to use Identory for profile creation:







![]()
We have created a single profile manually, now to enable the generation of large scale profiles or work with temporary profiles, simply open the dropdown next to the creation button and select the required option.

A careful analysis of the workings of this anti-detect tool alongside that of other software designed for the same purpose gives strong and weak points. Identory browser pros and cons are presented in the form of the table below.
|
Advantages |
Disadvantages |
|---|---|
|
+ Complete confidentiality is provided by local data storage, the absence of hidden requests, and the use of TOR + Other features: the automation of cookies, as well as the manual form emulation, and the advanced settings for running and stopping the profiles + High performance level + Unlimited profiles + API for integration with other applications and advanced automated processes + A set of more than a million unique fingerprints |
- Lacks features that make collaboration easier - No trial or free version is available - Doesn’t have the ability to set sync for multiple windows or tabs - Lacks the ability to perform simple automation such as RPA |
Following the Identory overview, it is feasible to assume that this tool is mainly intended for singular use, owing to the omission of profile transfer functions and rights assignment provisions which allow for shared collaboration on profiles. A purchase of additional user slots who can log into the browser on other devices is the only way to execute teamwork.
But anyway, the browser is appreciated in other areas, such as traffic arbitration, SMM, eCommerce, and other similar fields, because the fingerprinting and other auxiliary features enable detailed customization. With the help of these features, profiles that are created are highly convincing to the target resources and are not flagged by anti-fraud systems. The API enables setting up advanced automation features that require complex interactions between the app and other software. For these reasons, Identory is, indeed, the preferred app in professional settings.
Identory is a modern antidetect solution capable of advanced custom settings. The profiles created can easily bypass detection checks on services like Pixelscan, BrowserLeaks, WHOER because these services consider those IDs authentic, thus allowing multi-accounting on various web resources without the risk of getting flagged as a top-level threat.
In addition, the unique identifying feature of the browser is the method of storing and encrypting the user's information which enhances confidentiality and data protection. Therefore, it can be used for guaranteeing anonymity in professional dealings.
Comments: 0